Broken Authentication and Session Management
Step-by-Step Explanation:
📌 1st Scenario: Old Session Does Not Expire After Password Change
📌 2nd Scenario: Session Hijacking (Intended Behaviour)
Impact: If the attacker gets the cookies of the victim it will lead to an account takeover.
📌 3rd Scenario: Password Reset Token Does Not Expire (Insecure Configuration)
📌 4th Scenario: Server Security Misconfiguration
→ Lack of security headers → Cache control for a security page
📌 5th Scenario: Broken Authentication to Email Verification Bypass (P4)
Category: P4 >> Broken Authentication and Session Management >> Failure to Invalidate Session >> On Password Reset and/or Change
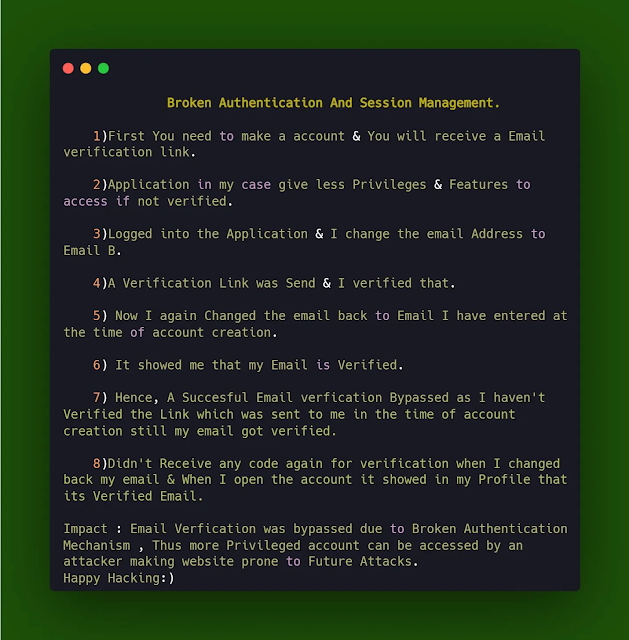
📌 6th Scenario: Email Verification Bypass (P3/P4)
Impact: Email Verification Bypass
📌 7th Scenario: Old Password Reset Token Not Expiring upon Requesting New One (Sometimes P4)
Note: Some companies won’t accept this as a valid issue.
📌 8th Scenario: Password Reset Token Not Expiring After Password Change (P4)
Thank you guys for reading this post -- Happy Hunting 🐞
Resources:
Google & YouTube
Authors:
Farhan & Raiders
Support me: If you'd like to support me, buy me a cup of Coffee ☕













0 Comments